Brand protection has become more challenging than ever, but the history of domain ownership can help organizations strengthen their strategies. Imitators and counterfeiters indeed abound in the digital world since it’s relatively easy to do. Threat actors only need to think of variations of a brand or domain name and register them.
Consider Microsoft, for example. There are more than 250 ways the seven-letter brand name can be misspelled or varied. Variations include the use of Punycode characters that look like Latin characters. If you factor in the 1,000 generic top-level domains (gTLDs), then there could be more than 250,000 ways a threat actor can imitate microsoft[.]com.
How can domain ownership history help organizations with their brand protection strategies, specifically in combating cybersquatting?
Check the Domain Ownership History of a Cybersquatting Domain
A Microsoft Azure client who hypothetically receives an email from info@microsoftt[.]com asking him/her to reset his/her password can innocently click a malware-planting link. Such an action can ultimately result in a data breach, and aside from the potential monetary loss, Microsoft or any imitated company can suffer reputational damage.
As such, before cybersquatting domains may end up weaponized, organizations have the option to register them. That is usually the tactic of large corporations, such as Bank of America, which registered more than 8,000 lookalike domains. But what happens when you find out that the cybersquatting domain is already owned by someone else whose details are redacted for privacy? A look into historical WHOIS data could be the key.
The WHOIS records of cybersquatting domain microsoftt[.]com, for instance, only shows that the registrar is eName Technology Co., Ltd, and the registrant is from Hu Nan, China. The registrant name, street address, email address, and phone number are all hidden.
How can Microsoft negotiate the purchase of the domain with the registrant? Using WHOIS history tools, they can find clues to uncover the registrant’s identity. For microsoftt[.]com, our WHOIS history tool was able to unearth its domain ownership history as far back as July 2012.
And although the domain has undergone more than 500 updates, we were able to find out that the same registrant owned it from July 2012 until January 2018. His last name is Quan with a registrant address in China. After that, the WHOIS records were redacted.
Assuming the registrant remained the same, Microsoft can then try to negotiate with him to obtain the cybersquatting domain. It can also file a Uniform Domain Name Dispute Resolution Policy (UDRP) case with the World Intellectual Property Organization (WIPO).
Look into the History of Domain Ownership Before Buying a Domain
Another way that domain ownership history can help enhance brand protection is by using WHOIS history tools in investigating a domain before purchase. Finding a domain for your product or service should not end with checking its availability. You also have to make sure that the chosen domain name does not have a checkered past.
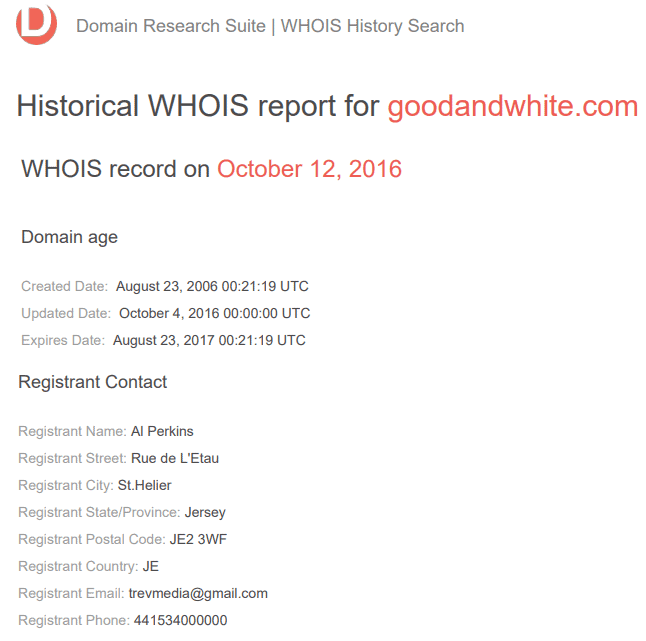
If you are hypothetically planning to use goodandwhite[.]com for your interior design business, for example, you would want to check its history of domain ownership before buying it. After all, the domain name will be tied to your services and brand once you purchase it.
WHOIS history would reveal that two different people owned the domain goodandwhite[.]com within about four years. From June 2012 to January 2016, it was owned by someone in Connecticut, U.S. The registrant may have neglected to renew the domain’s registration when it expired because in October 2016, the prolific cybersquatter Al Perkins (or someone with the same name) was able to grab the domain.
Al Perkins is, among other individuals, a known cybersquatter grabbing domain names from businesses and redirecting these to adult websites as a technique to pressure the original owner to repurchase the domains at a higher price. An interior design company that banks on its reputation may not want to use a domain that has ties to adult sites and was part of an extortion scheme.
The history of domain ownership plays an essential role in protecting your brand—be it from cybersquatters who can weaponize lookalike domains or seemingly excellent business opportunities with a checkered past.
About the Author
Jonathan Zhang is the founder and CEO of WhoisXML API—a domain and IP data intelligence provider that empowers all types of cybersecurity enterprises to build better products and achieve greater network security with the most comprehensive domain, IP, DNS, and cyber threat intelligence feeds. WhoisXML API also offers a variety of APIs, tools, and capabilities, including Threat Intelligence Platform (TIP) and Domain Research Suite (DRS).